

Editor
2nd Aug 2025
Difficulty: Easy
Machine Author(s): kavigihan & TheCyberGeek
Successfully Pwned Editor
nquangit has successfully completed and pwned this machine on Hack The Box.
Machine Information
None.
Enumeration
Every journey begins with a single step, and every attack starts by gathering as much information as possible about the target. As the ancient maxim goes, “Know your enemy and know yourself, and in a hundred battles you will never be defeated.”
Nmap scan
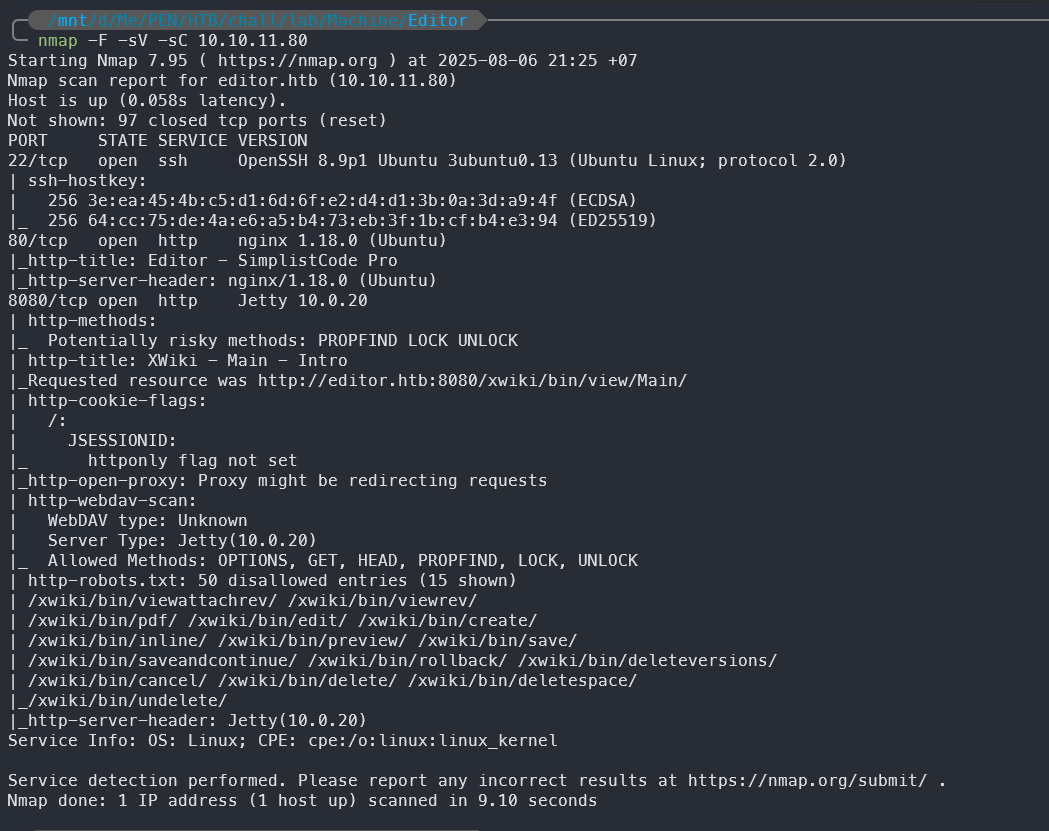
# Nmap 7.95 scan initiated Wed Aug 6 12:54:39 2025 as: /usr/lib/nmap/nmap --privileged -F -sV -sC -Pn -oN nmap.txt 10.10.11.80
Nmap scan report for 10.10.11.80
Host is up (0.061s latency).
Not shown: 97 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.13 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 3e:ea:45:4b:c5:d1:6d:6f:e2:d4:d1:3b:0a:3d:a9:4f (ECDSA)
|_ 256 64:cc:75:de:4a:e6:a5:b4:73:eb:3f:1b:cf:b4:e3:94 (ED25519)
80/tcp open http nginx 1.18.0 (Ubuntu)
|_http-title: Did not follow redirect to http://editor.htb/
|_http-server-header: nginx/1.18.0 (Ubuntu)
8080/tcp open http Jetty 10.0.20
|_http-server-header: Jetty(10.0.20)
| http-methods:
|_ Potentially risky methods: PROPFIND LOCK UNLOCK
|_http-open-proxy: Proxy might be redirecting requests
| http-title: XWiki - Main - Intro
|_Requested resource was http://10.10.11.80:8080/xwiki/bin/view/Main/
| http-webdav-scan:
| WebDAV type: Unknown
| Server Type: Jetty(10.0.20)
|_ Allowed Methods: OPTIONS, GET, HEAD, PROPFIND, LOCK, UNLOCK
| http-robots.txt: 50 disallowed entries (15 shown)
| /xwiki/bin/viewattachrev/ /xwiki/bin/viewrev/
| /xwiki/bin/pdf/ /xwiki/bin/edit/ /xwiki/bin/create/
| /xwiki/bin/inline/ /xwiki/bin/preview/ /xwiki/bin/save/
| /xwiki/bin/saveandcontinue/ /xwiki/bin/rollback/ /xwiki/bin/deleteversions/
| /xwiki/bin/cancel/ /xwiki/bin/delete/ /xwiki/bin/deletespace/
|_/xwiki/bin/undelete/
| http-cookie-flags:
| /:
| JSESSIONID:
|_ httponly flag not set
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Wed Aug 6 12:54:50 2025 -- 1 IP address (1 host up) scanned in 11.25 seconds
With the Nmap scan, we can see that the machine has two open ports: SSH on port 22 and HTTP on port 80 and 8080. The HTTP service is running Nginx version 1.18.0.
From the result, we also know the hostname for the http service is editor.htb.
Based on my gut feeling and after examining the scan results, I was confident that the HTTP service on port 8080 was the one to target—and I was right. We can safely ignore the HTTP service on port 80.
Additional: The service running on port 8080 is configured as a virtual host under the name wiki.editor.htb. You can uncover this hostname either by performing a quick subdomain enumeration against the target or by crawling the web application hosted on port 80.
nuclei
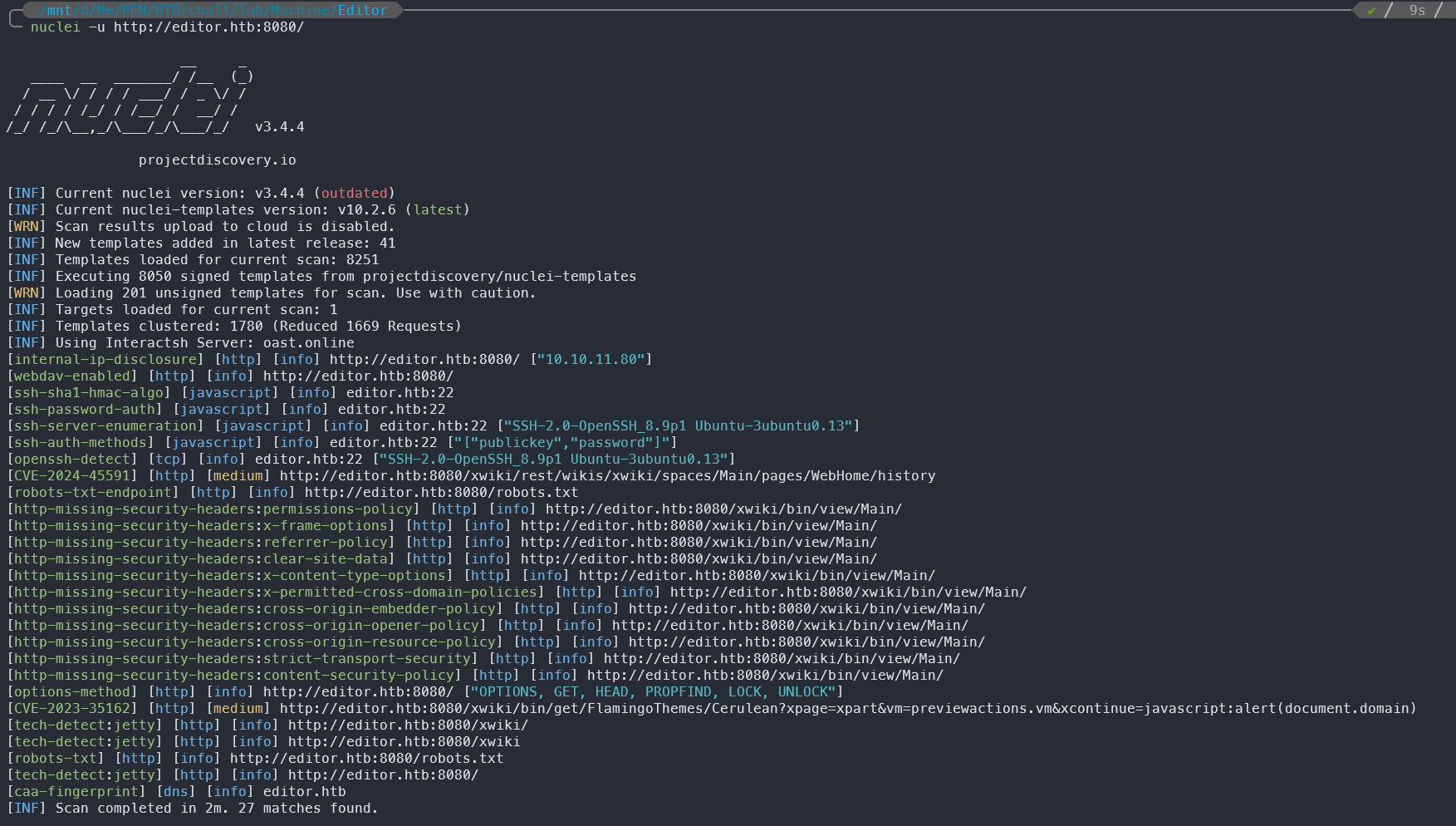
[internal-ip-disclosure] [http] [info] http://editor.htb:8080/ ["10.10.11.80"]
[webdav-enabled] [http] [info] http://editor.htb:8080/
[ssh-sha1-hmac-algo] [javascript] [info] editor.htb:22
[ssh-password-auth] [javascript] [info] editor.htb:22
[ssh-server-enumeration] [javascript] [info] editor.htb:22 ["SSH-2.0-OpenSSH_8.9p1 Ubuntu-3ubuntu0.13"]
[ssh-auth-methods] [javascript] [info] editor.htb:22 ["["publickey","password"]"]
[openssh-detect] [tcp] [info] editor.htb:22 ["SSH-2.0-OpenSSH_8.9p1 Ubuntu-3ubuntu0.13"]
[CVE-2024-45591] [http] [medium] http://editor.htb:8080/xwiki/rest/wikis/xwiki/spaces/Main/pages/WebHome/history
[robots-txt-endpoint] [http] [info] http://editor.htb:8080/robots.txt
[http-missing-security-headers:permissions-policy] [http] [info] http://editor.htb:8080/xwiki/bin/view/Main/
[http-missing-security-headers:x-frame-options] [http] [info] http://editor.htb:8080/xwiki/bin/view/Main/
[http-missing-security-headers:referrer-policy] [http] [info] http://editor.htb:8080/xwiki/bin/view/Main/
[http-missing-security-headers:clear-site-data] [http] [info] http://editor.htb:8080/xwiki/bin/view/Main/
[http-missing-security-headers:x-content-type-options] [http] [info] http://editor.htb:8080/xwiki/bin/view/Main/
[http-missing-security-headers:x-permitted-cross-domain-policies] [http] [info] http://editor.htb:8080/xwiki/bin/view/Main/
[http-missing-security-headers:cross-origin-embedder-policy] [http] [info] http://editor.htb:8080/xwiki/bin/view/Main/
[http-missing-security-headers:cross-origin-opener-policy] [http] [info] http://editor.htb:8080/xwiki/bin/view/Main/
[http-missing-security-headers:cross-origin-resource-policy] [http] [info] http://editor.htb:8080/xwiki/bin/view/Main/
[http-missing-security-headers:strict-transport-security] [http] [info] http://editor.htb:8080/xwiki/bin/view/Main/
[http-missing-security-headers:content-security-policy] [http] [info] http://editor.htb:8080/xwiki/bin/view/Main/
[options-method] [http] [info] http://editor.htb:8080/ ["OPTIONS, GET, HEAD, PROPFIND, LOCK, UNLOCK"]
[CVE-2023-35162] [http] [medium] http://editor.htb:8080/xwiki/bin/get/FlamingoThemes/Cerulean?xpage=xpart&vm=previewactions.vm&xcontinue=javascript:alert(document.domain)
[tech-detect:jetty] [http] [info] http://editor.htb:8080/xwiki/
[tech-detect:jetty] [http] [info] http://editor.htb:8080/xwiki
[robots-txt] [http] [info] http://editor.htb:8080/robots.txt
[tech-detect:jetty] [http] [info] http://editor.htb:8080/
[caa-fingerprint] [dns] [info] editor.htb
As mentioned above, I will focus exclusively on the HTTP service running on port 8080 wiki.editor.htb. Using Nuclei for reconnaissance, we flagged several noteworthy issues—missing security headers, a robots.txt file, and the like—but none proved sufficiently critical to warrant deeper exploitation.
Additionally, Nuclei surfaced two CVEs rated with a MEDIUM impact: one reflecting a potential XSS vector and the other revealing change-history information disclosure. While it’s worth briefly validating these findings, they offer limited value for further exploitation.
Manual inspection
Next, we’ll switch to manual browser-based exploration to review the available pages, validate our scan findings, and gather additional context.
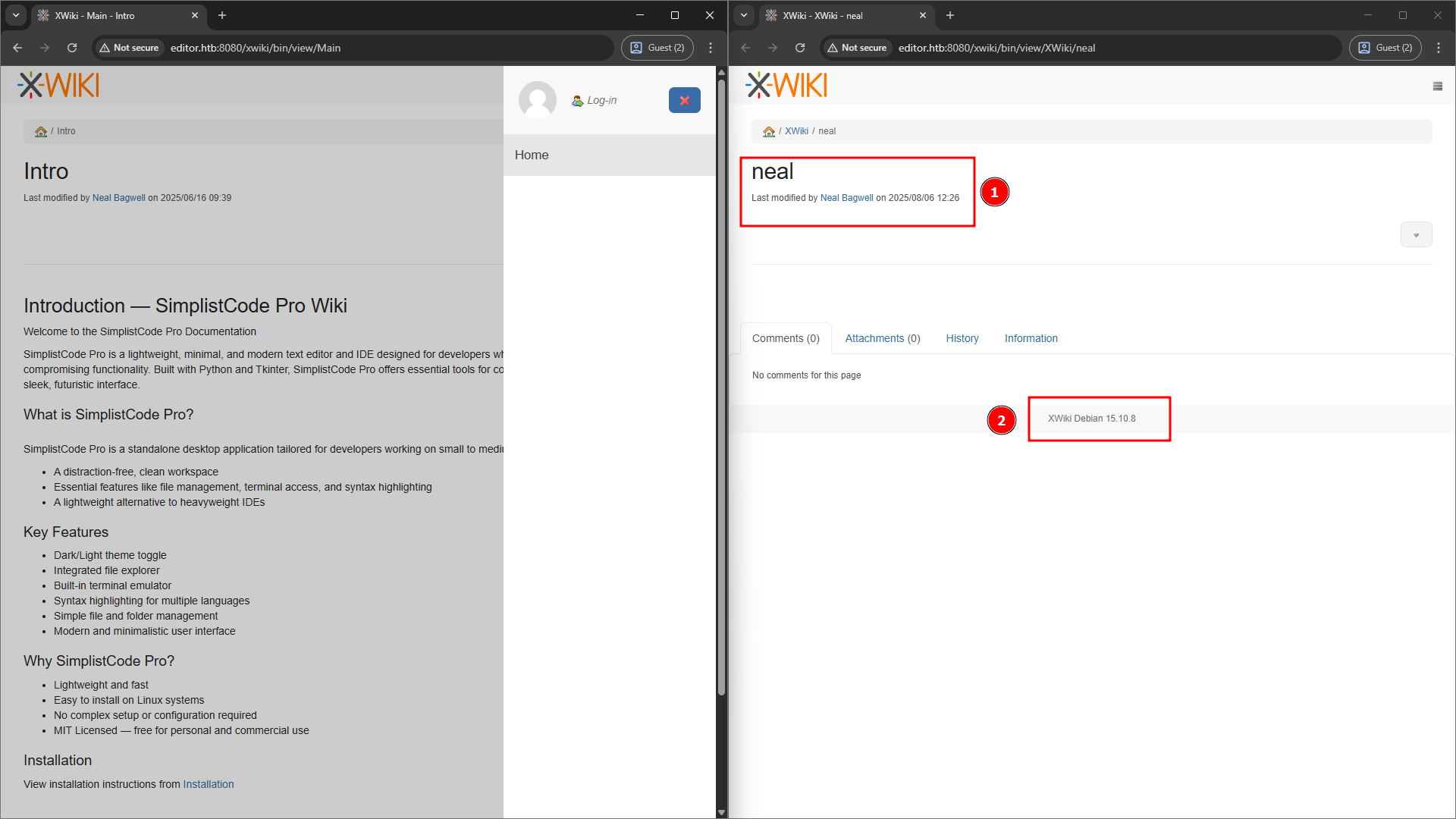
Upon inspection, it’s immediately clear that the target is running XWiki version 15.10.8, it might be a known CVE to exploit here.
We also discovered a user account neal (full name: Neal Bagwell). While it’s good to note, this information doesn’t appear to offer an obvious exploitation path—at least not for now.
Finding CVE
Armed with the discovery that our target is running XWiki version 15.10.8, we can pivot to some targeted Google searches to determine if this release suffers from any known CVEs.
A quick search reveals a relevant 2025 CVE as follows:
Part of this article is encrypted with password:
⚠️ Active Machine Notice
This box is currently active on HackTheBox. Once retired, this article will be published for public access as per HackTheBox's policy on publishing content from their platform.
💬 For hints and assistance, join me and the community in the HackTheBox Discord server.
Good luck!


Leave a comment