

Outbound
12th Jul 2025
Difficulty: Easy
Machine Author(s): TheCyberGeek
Successfully Pwned Outbound
nquangit has successfully completed and pwned this machine on Hack The Box.
Machine Information
As is common in real life pentests, you will start the Outbound box with credentials for the following account tyler / LhKL1o9Nm3X2
Enumeration
nmap Scan
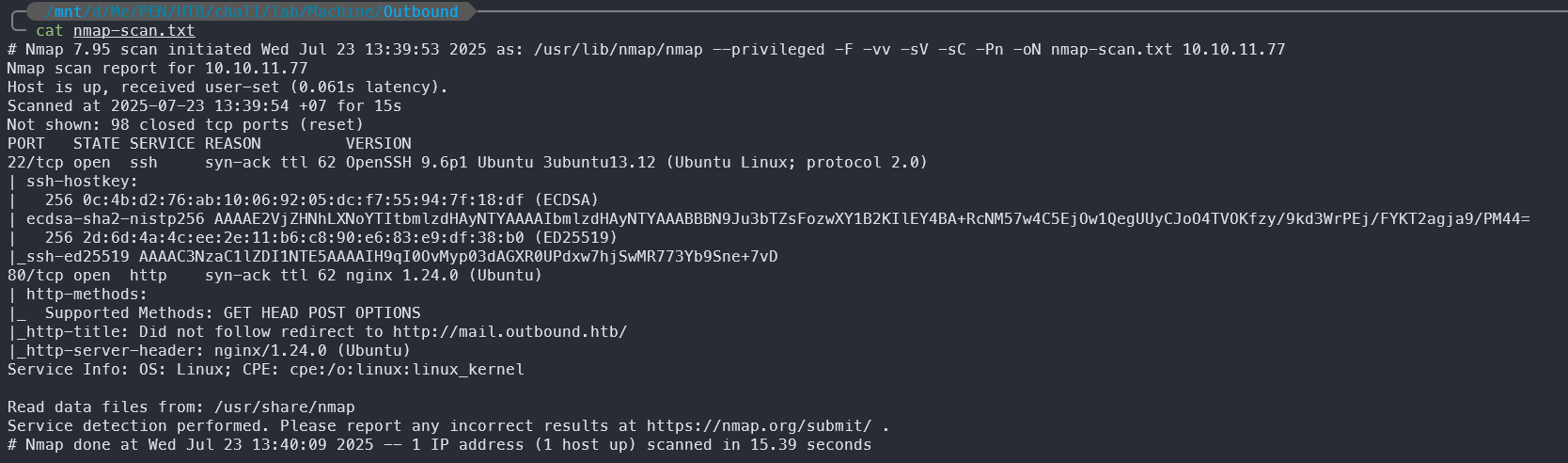
# Nmap 7.95 scan initiated Wed Jul 23 13:39:53 2025 as: /usr/lib/nmap/nmap --privileged -F -vv -sV -sC -Pn -oN nmap-scan.txt 10.10.11.77
Nmap scan report for 10.10.11.77
Host is up, received user-set (0.061s latency).
Scanned at 2025-07-23 13:39:54 +07 for 15s
Not shown: 98 closed tcp ports (reset)
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 62 OpenSSH 9.6p1 Ubuntu 3ubuntu13.12 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 0c:4b:d2:76:ab:10:06:92:05:dc:f7:55:94:7f:18:df (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBN9Ju3bTZsFozwXY1B2KIlEY4BA+RcNM57w4C5EjOw1QegUUyCJoO4TVOKfzy/9kd3WrPEj/FYKT2agja9/PM44=
| 256 2d:6d:4a:4c:ee:2e:11:b6:c8:90:e6:83:e9:df:38:b0 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIH9qI0OvMyp03dAGXR0UPdxw7hjSwMR773Yb9Sne+7vD
80/tcp open http syn-ack ttl 62 nginx 1.24.0 (Ubuntu)
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-title: Did not follow redirect to http://mail.outbound.htb/
|_http-server-header: nginx/1.24.0 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Read data files from: /usr/share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Wed Jul 23 13:40:09 2025 -- 1 IP address (1 host up) scanned in 15.39 seconds
With the Nmap scan, we can see that the target machine has two open ports:
- 22 (SSH) - OpenSSH version 9.6p1
- 80 (HTTP) - Nginx version 1.24.0
We can also see that the web server redirects to http://mail.outbound.htb/. Then we need to add this domain to our /etc/hosts file:
echo "ip_address mail.outbound.htb" | sudo tee -a /etc/hosts
Nuclei Scan
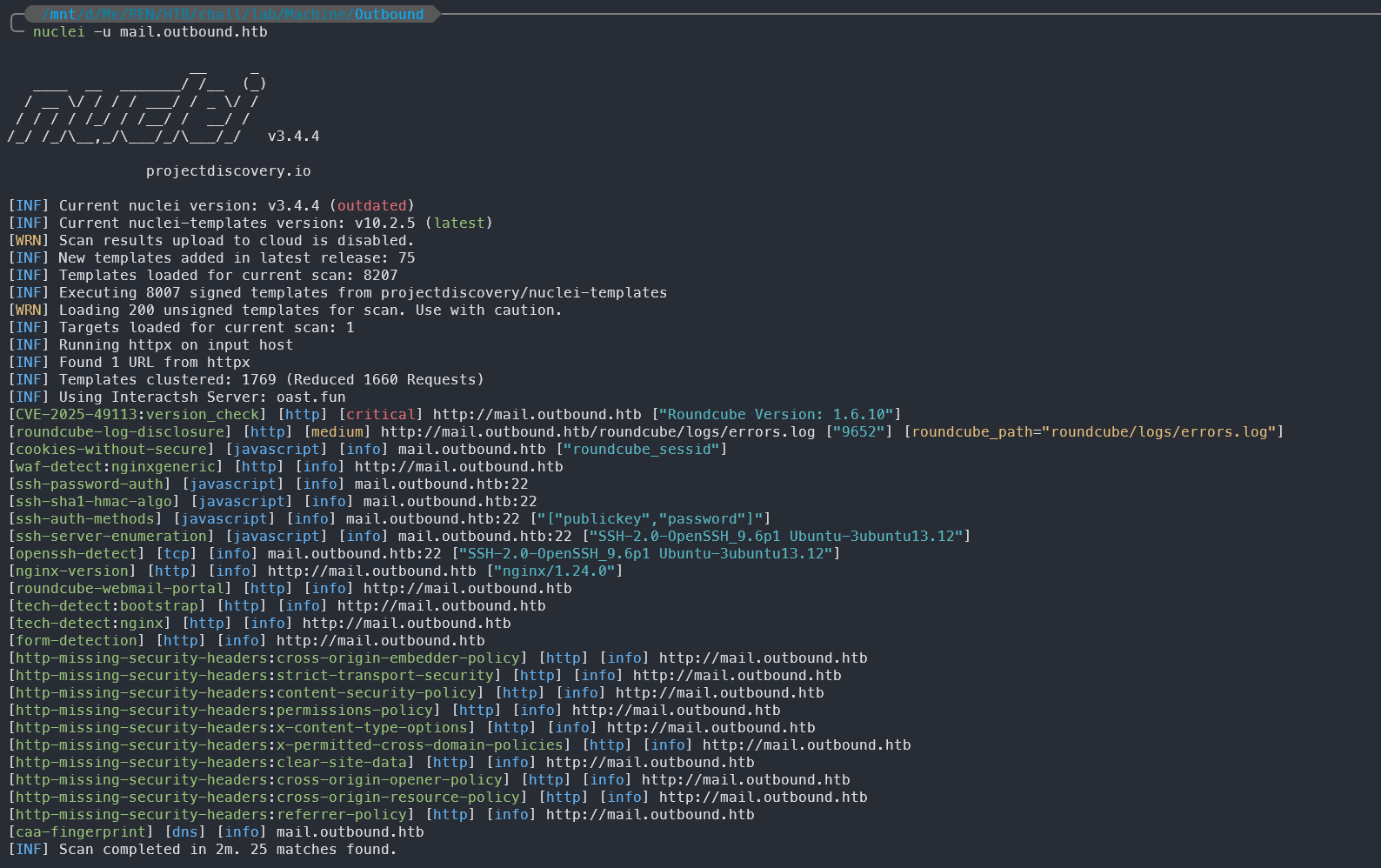
[CVE-2025-49113:version_check] [http] [critical] http://mail.outbound.htb ["Roundcube Version: 1.6.10"]
[roundcube-log-disclosure] [http] [medium] http://mail.outbound.htb/roundcube/logs/errors.log ["3971"] [roundcube_path="roundcube/logs/errors.log"]
[cookies-without-secure] [javascript] [info] mail.outbound.htb ["roundcube_sessid"]
[waf-detect:nginxgeneric] [http] [info] http://mail.outbound.htb
[ssh-password-auth] [javascript] [info] mail.outbound.htb:22
[ssh-server-enumeration] [javascript] [info] mail.outbound.htb:22 ["SSH-2.0-OpenSSH_9.6p1 Ubuntu-3ubuntu13.12"]
[ssh-sha1-hmac-algo] [javascript] [info] mail.outbound.htb:22
[ssh-auth-methods] [javascript] [info] mail.outbound.htb:22 ["["publickey","password"]"]
[openssh-detect] [tcp] [info] mail.outbound.htb:22 ["SSH-2.0-OpenSSH_9.6p1 Ubuntu-3ubuntu13.12"]
[form-detection] [http] [info] http://mail.outbound.htb
[nginx-version] [http] [info] http://mail.outbound.htb ["nginx/1.24.0"]
[roundcube-webmail-portal] [http] [info] http://mail.outbound.htb
[http-missing-security-headers:strict-transport-security] [http] [info] http://mail.outbound.htb
[http-missing-security-headers:content-security-policy] [http] [info] http://mail.outbound.htb
[http-missing-security-headers:permissions-policy] [http] [info] http://mail.outbound.htb
[http-missing-security-headers:x-content-type-options] [http] [info] http://mail.outbound.htb
[http-missing-security-headers:x-permitted-cross-domain-policies] [http] [info] http://mail.outbound.htb
[http-missing-security-headers:referrer-policy] [http] [info] http://mail.outbound.htb
[http-missing-security-headers:clear-site-data] [http] [info] http://mail.outbound.htb
[http-missing-security-headers:cross-origin-embedder-policy] [http] [info] http://mail.outbound.htb
[http-missing-security-headers:cross-origin-opener-policy] [http] [info] http://mail.outbound.htb
[http-missing-security-headers:cross-origin-resource-policy] [http] [info] http://mail.outbound.htb
[tech-detect:bootstrap] [http] [info] http://mail.outbound.htb
[tech-detect:nginx] [http] [info] http://mail.outbound.htb
[caa-fingerprint] [dns] [info] mail.outbound.htb
In the Nuclei scan results, we can see that the target machine is running Roundcube version 1.6.10, which is vulnerable to CVE-2025-49113. This vulnerability allows remote code execution by authenticated users because the _from parameter in a URL is not validated in program/actions/settings/upload.php, leading to PHP Object Deserialization.
It’s also worth noting that the Nuclei scan found a log file at roundcube/logs/errors.log, which may contain sensitive information.
Manual Inspection
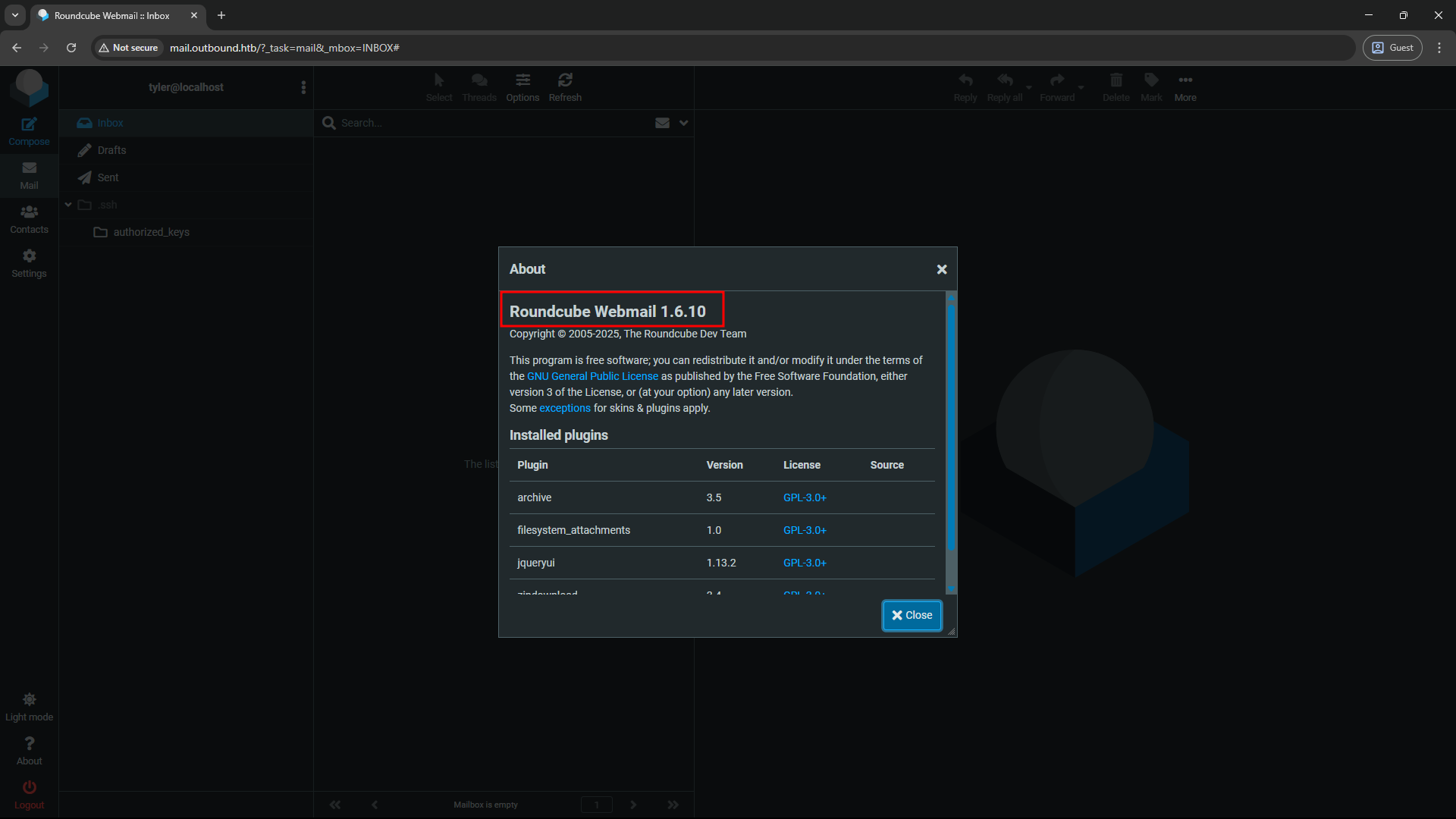
With the provided credentials tyler / LhKL1o9Nm3X2, we can log in to the Roundcube webmail interface at http://mail.outbound.htb/roundcube/. After logging in, we can confirm that the version is indeed 1.6.10 and that it is vulnerable to CVE-2025-49113.
Exploitation
Part of this article is encrypted with password:
⚠️ Active Machine Notice
This box is currently active on HackTheBox. Once retired, this article will be published for public access as per HackTheBox's policy on publishing content from their platform.
💬 For hints and assistance, join me and the community in the HackTheBox Discord server.
Good luck!


Leave a comment